Simply put, Steg is a steganography program. That is, it hides data, encrypted or otherwise, in something where you would not expect it to be hidden. In other programs of this nature for the Macintosh, such as Stego by Romana Machado or Paranoid by Nathan Mariels, the hidden message or data file is encoded by hiding it within the data of an image or sound file. Steg takes advantage of an interesting fact about Mac applications, and especially Applescript applicaitons in general - most applications do not contain a data fork. Using Resedit with Forker, this is quite easy to determine. What Steg does is take your text or other data-fork-based file, and insert it into the data fork of the program to be extracted at a later date... and since most people don't open their applications up and stare at the innards, it is a reasonably secure way to transmit information, provided the data is already encrypted.
For instance, here's a quick example. Take on of the sample host programs included in the Steg folder, which you can use as a "host" for your data files. Since it acts like a regular application, it appears to be just that, but a message can easily be hidden away inside.

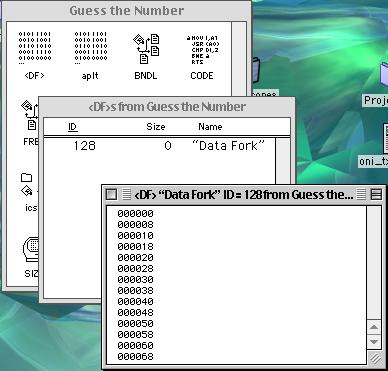
The above picture shows the data fork of the regular Guess the Number application. Notice that since there is no standard data fork, no data has been entered yet.
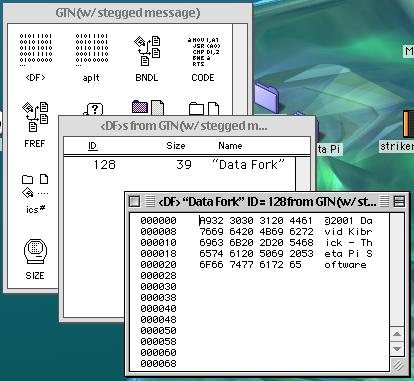
This picture represents a plain-text message inserted into the data fork of the program (GTN w/ stegged message). As you can see, the plain text is clearly visible. Should anyone get suspicious and open up an application with a message inserted in the clear, the message would be immediately available to the interceptor.
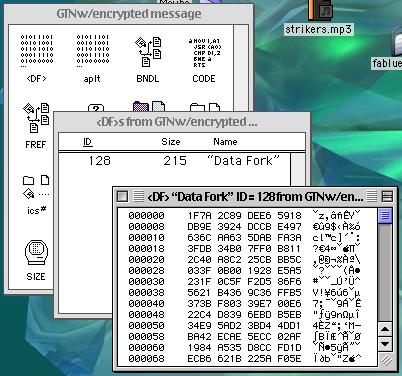
This image represents a passage encoded with BlockEnc inserted into the data fork (GTN w/ encrypted message). Not only is the text unreadable to anyone who happens to come across it, the random characters appear to be unintelligable computer data, so that most people would simply assume the program had a regular data fork, and ignore the encrypted data. If you want, you can use deSteg to extract the message, then use the included code block and the password "Steg!" to read the hidden message.
You can either directly enter data into Steg or copy data from the clipboard, or drop the file you want to hide onto the Steg program. Next, choose the application or non-data-fork file that you want to hide your data in. WARNING: If the file you choose does contain a data fork, Steg could corrupt it and cause the program to malfunction. Check all applications with Resedit or HexEdit first to make sure that the data fork is, in fact, empty. Once you choose the file, you can not directly undo it, so make sure you copy the application in question before trying to Steg it.
To deSteg a file, simply drop it on deSteg, or select it from the dialog. deSteg will then extract and output the imbedded message. Again, a simple warning - if you deSteg a file that contains a real data fork, you will probably get a large text file with completely nosensical characters, and no amount of decrypting will reveal any sort of message.
Steg is not a perfect program. Since anyone with deSteg could potentially extract your data, make sure that it is encrypted as well as Stegged. Also, though this has not been tested, some virus checkers may get confused with mysterious data forks and cause a virus alert, and some people will not download attachments on principal, much less if they are told that the file has been "tampered with." So, keep in mind that Steg is not the last word in file security, but it's a good attempt that should foil most prying eyes.
1.0 - First release. Looks good so far, but no rigorous testing has been done, so use at your own risk.
©2001 David Kibrick. You may use this program free of charge, and you may redistribute this program, as long as you do not charge for it, and as long as it is maintained in its entire and original version.
Please remember to contact me if you have any questions, comments, gripes, or bugs you want to report. Also, this is the first time doing documentation in this format - tell me if you like this better, or whether you would rather deal with bare-bones text files.
Website: http://www.scshop.com/~thetapi/tindex.html
Email: thetapi@scshop.com
The background image for the tutorial pictures is "crystalline.jpg" by David Kibrick. You can download it for your desktop by clicking here.